Iran oil fires raise cyber sabotage fears


Iran’s cyberspace security authorities are looking into possible sabotage by the US or Israel following a recent string of fires in Iranian oil and gas facilities.
Energy officials have already ruled out deliberate criminal activity as being the cause of the blazes which incurred significant financial damage but suspicion persists among other authorities.
Secretary of Iran’s Supreme National Cyberspace Council Abolhasan Firoozabadi says a team of experts will be having a look at the possibility of cyberattacks as a possible cause.
“Special teams will be sent to the afflicted sites to study the possibility of cyber systems having a role in the recent fires,” he said on Wednesday.
The investigation comes in the wake of at least three fires at petrochemical and oil installations and another massive blaze on a 42-inch gas pipeline in recent weeks.
The worst of the blazes hit Bu Ali Sina petrochemical refinery complex in the southwest city of Bandar Mahshahr last month, seriously damaging its paraxylene unit.
Another fire broke out at the Bistoon petrochemical plant in Kermanshah in western Iran after a fault at the facility’s power transmission system, followed by two blazes at Iran’s largest oil refinery in Abadan and on a gas transmission line in the Shiraz province which left one person dead.
While technical faults and human error have been identified as the immediate cause by the Ministry of Petroleum, cyberspace security authorities have to delve deeper into the control systems to ensure they have not been tampered with.
Iran experienced the first cyberattack on its main oil export terminal and on the Petroleum Ministry itself in April 2012 when a virus was detected inside the control systems of Kharg Island which handles the bulk of Iranian crude oil exports.
The attack, which authorities said was traced back to the US, forced the ministry to disconnect computer systems controlling other oil facilities.
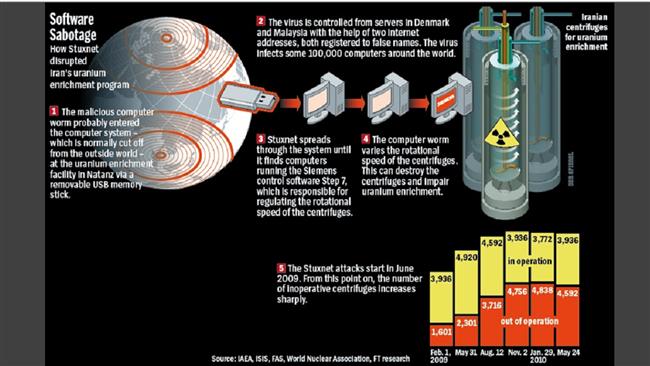
But the most high-profile cyberattack against Iran was discovered in 2010 after the Stuxnet virus, designed to subvert industrial systems, targeted the country’s nuclear energy program.
The malware had been coded to interfere with control systems at an Iranian uranium enrichment facility so that its centrifuges spin out of control.
Iranian authorities blamed the attack on the US and Israel and a number of American institutions in the know of the matter supported the allegation.
The Stuxnet virus has become the most serious case of “state cyber-terrorism” because of its complexity and sabotage of sensitive properties.
Later that year, Iran identified another virus called Duqu which had been designed to disrupt industrial processes.
In February, the New York Times reported that the US had developed an elaborate plan for a cyberattack on Iran in the early years of the Obama administration.
The plan, code-named Nitro Zeus, was devised to disable Iran’s air defenses, communications systems and crucial parts of its power grid, the paper said.
It “was shelved, at least for the foreseeable future, after the nuclear deal struck between Iran and six other nations last summer was fulfilled,” the NY Times said.

The existence of Nitro Zeus was uncovered in the course of reporting for “Zero Days,” a documentary by Oscar-winning director Alex Gibney shown at the Berlin Film Festival in February.
Nitro Zeus reportedly had its roots in the Bush administration but took on new life in 2009 and 2010 just as Obama asked United States Central Command to develop a detailed military plan for Iran in case diplomacy failed.
The plan included efforts to infuse Iran’s computer networks with “implants” that could be used to monitor the country’s activities and, if ordered by Obama, to attack its infrastructure, the report said.




